The hackers’ quantum leap
EXTERNAL ARTICLE
Quantum computing will light the way for hackers to identify and attack air-gapped servers — high-security computers once thought immune to data theft — new analysis by the cybersecurity consultants Cystel has revealed.

How can hackers gain access to air-gapped computers?
EXTERNAL ARTICLE
Quantum computing will light the way for hackers to identify and attack air-gapped servers — high-security computers once thought immune to data theft — new analysis by the cybersecurity consultants Cystel has revealed.
Atomic wallet has been exposed
EXTERNAL ARTICLE
The Atomic Wallet community has been rocked by a recent breach that may have been orchestrated by Lazarus, the notorious North Korean hacking syndicate, as reported by blockchain intelligence experts Elliptic.
Cystel’s Sarma comments on UK cybersecurity threats
EXTERNAL ARTICLE
National cyber strategy must focus more on game-changing quantum technology risk, according to Cystel’s Dr Meera Sarma. Sarma, the CEO of cybersecurity consultancy Cystel, says: “Future-proofing our digital economy is vital in the face of increasing numbers of state-sponsored threats and individual attacks on UK companies and infrastructure.”
Zhong’s heist of 50,000 Bitcoin gives way to new ‘industrial’ era in crypto crime
EXTERNAL ARTICLE
Artificial intelligence and quantum computing are poised to accelerate cryptocurrency crime. Surging number of hacks poses existential challenge to DeFi
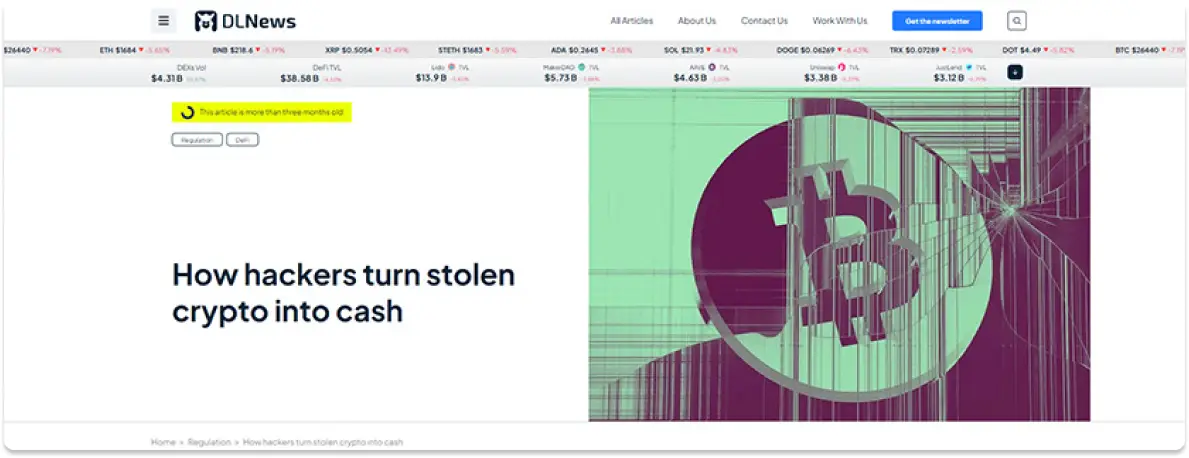
How hackers turn stolen crypto into cash
EXTERNAL ARTICLE
Cybercriminals steal billions of cryptocurrencies every year through ransomware attacks, exploits and hacks. But theft is just the first step in illicit crypto activity. Perpetrators then use a web of crypto mixers, chain-hopping services, scam tokens, and exchanges to launder their loot, hide their tracks, and eventually cash out.
Hackers Quantum Leap: Impregnable Off-Grid Computers
EXTERNAL ARTICLE
Quantum computing will light the way for hackers to identify and attack air-gapped servers — high-security computers once thought immune to data theft — new analysis by the cybersecurity consultants Cystel has revealed
On notice about quantum computing
EXTERNAL ARTICLE
Quantum computing will light the way for hackers to identify and attack air-gapped servers — high-security computers once thought immune to data theft, cybersecurity consultants suggest.
Impregnable off-grid computers exposed by their power supply
EXTERNAL ARTICLE
Quantum computing will light the way for hackers to identify and attack air-gapped servers — high-security computers once thought immune to data theft — new analysis by cybersecurity consultants Cystel has revealed.
Five Things the Royal Mail Ransom Transcript Leak Taught Us About Ransom Negotiations
EXTERNAL ARTICLE
The exposure of the leaked ransom negotiation logs may suggest a failed negotiation, but on closer inspection, many consider it a well-played hand by Royal Mail






CONTACT INFORMATION
UK Tel: +44 333 1223 372
USA Tel: +1 833 838 6754
LATAM Tel: +52 (55) 5335 0800
E: info@cystel.org
WHERE TO FIND US
Clavering House, Clavering Place, Newcastle Upon Tyne, England, UK NE1 3NG
2001 L STREET N.W. SUITE 500, WASHINGTON, DC, 20036
Rio Lerma 232, Piso 23 (Torre Diana), Ciudad de Mexico, CP 06500, Mexico
